Microsoft Sentinel Integration
STIX v2.1 and TAXII Protocol
About this integration
The following instructions will guide you through the process of configuring the RST Threat Feed in Microsoft Sentinel using the STIX v2.1 data format and the TAXII protocol. This integration allows you to populate the standard threat intelligence table in Microsoft Sentinel automatically. Please note that this integration needs to be configured per feed for each Sentinel instance. This integration will only pull attributed indicators.
Microsoft website: https://learn.microsoft.com/en-us/azure/sentinel/connect-threat-intelligence-taxii
Prerequisites
Ensure you have the necessary permissions to perform the following tasks:
- Template Spec Contributor role at the resource group level for installation, update, and deletion of content or solutions in the Content Hub
- Read and write permissions to the Microsoft Sentinel workspace to store threat indicators.
Configuration Steps
- Obtain the API Root URL and Collection IDs:
- Contact the RST Cloud Support Team to request the API Root URL and Collection IDs for the RST Threat Feed.
- Install the Threat Intelligence solution in Microsoft Sentinel:
- Navigate to the Azure portal and access the Microsoft Sentinel service.
- Choose the workspace where you want to import the threat indicators.
- Select "Content hub" from the menu.
- Locate and select the "Threat Intelligence" solution.
- Click the "Install/Update" button to install the solution. Follow the on-screen instructions if any additional steps are required.
- Enable the Threat Intelligence - TAXII data connector:
-
- Go to the Data connectors menu in Microsoft Sentinel.
- Locate and select the "Threat Intelligence - TAXII" data connector, then click the "Open connector page" button.
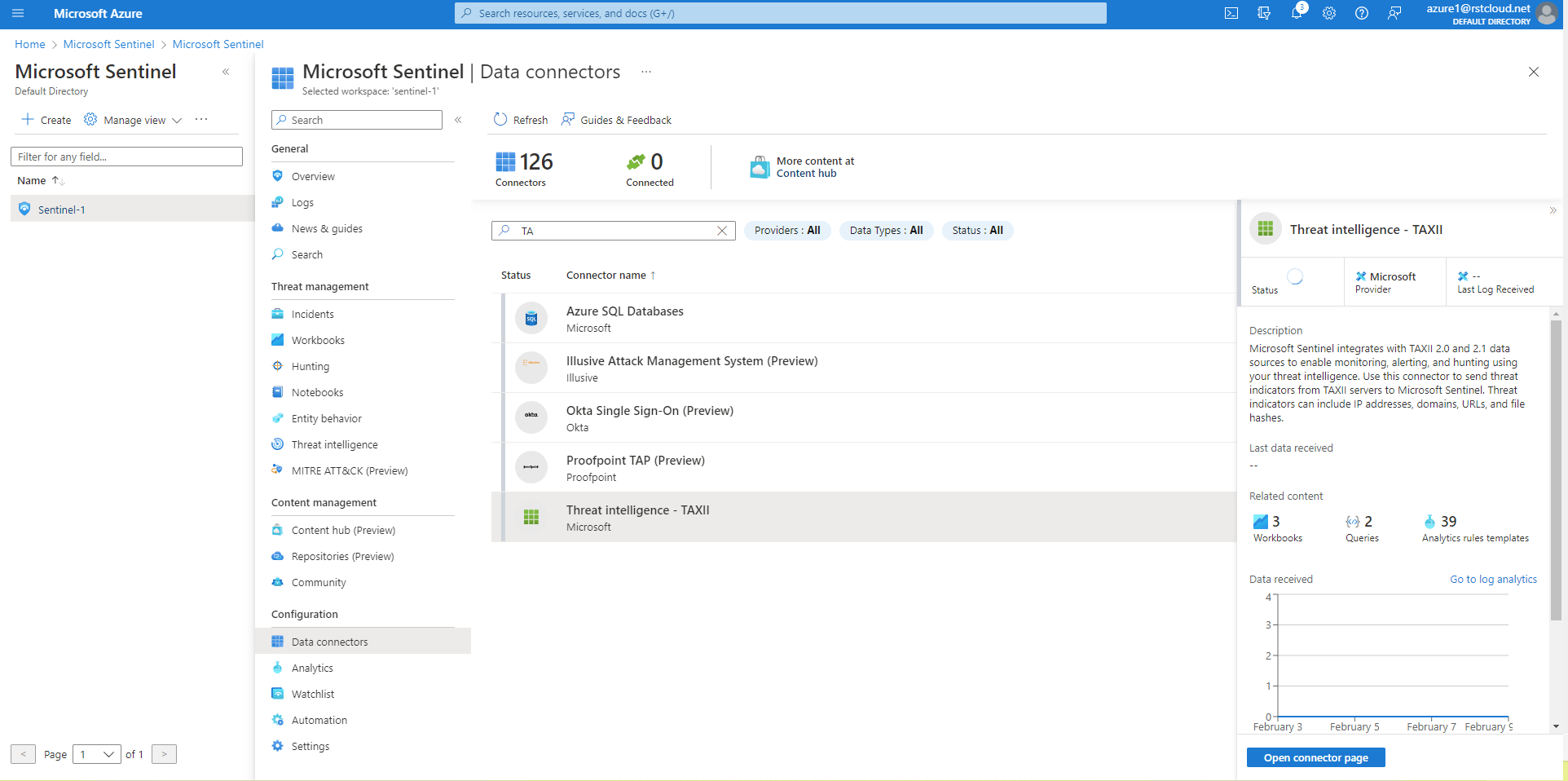
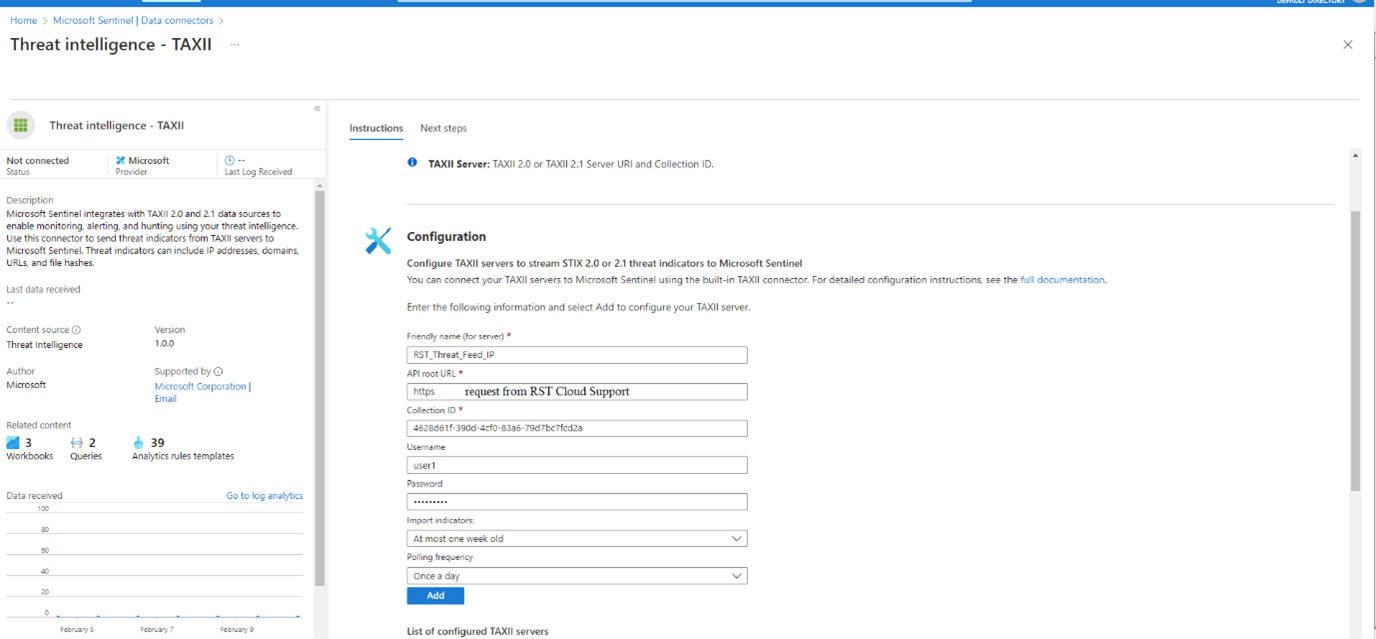
- On the connector page, enter the following details:
- Friendly Name: Provide a descriptive name for the RST Threat Feed Collection, for example: rst_threat_feed_ip, rst_threat_feed_domain, rst_threat_feed_url, rst_threat_feed_hash
- API Root URL: Obtain this URL from the RST Cloud Support Team.
- Collection ID: Use the appropriate Collection ID based on the feed type:
- xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx (please reach out RST Cloud support team to get the IDs for you)
- Username / Password: Contact RST Cloud Support Team. Trial credentials are only to be requested by email.
- Polling Frequency: Set it to "Once a day".
- Import indicators: At most one week old
- Click the "Add" button to save the configuration.
-
- Verify the connection:
Within a few minutes, threat indicators from the RST Threat Feed should start flowing into your Microsoft Sentinel workspace. To access the new indicators, go to the Threat intelligence blade in the Microsoft Sentinel navigation menu.
Note: It's recommended to import threat indicators that are at most one week old. Full data set is not available via TAXII/STIX integration. Use the standard API to fetch all possible indicators.
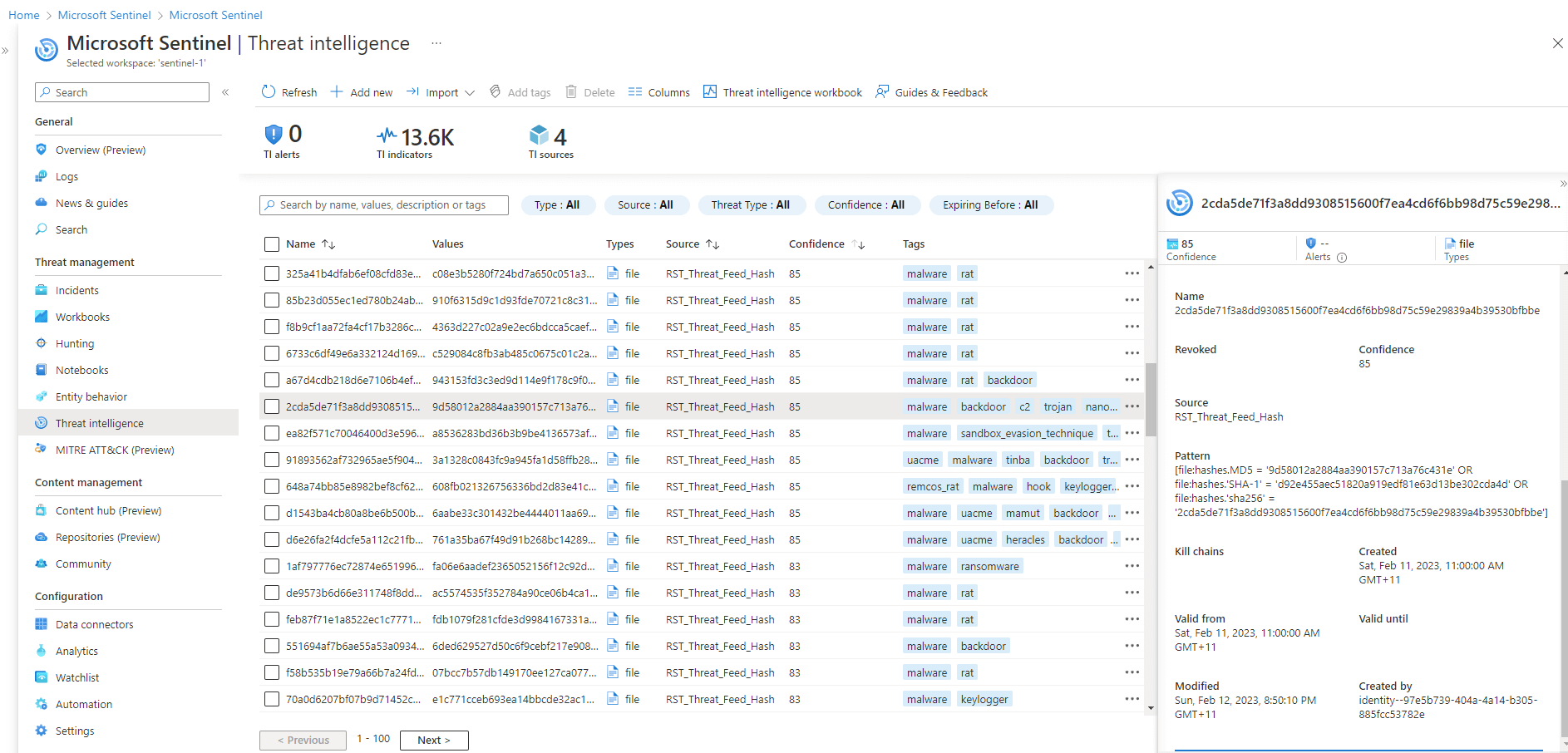
Congratulations! You have successfully configured the RST Threat Feed in Microsoft Sentinel using STIX v2.1 and the TAXII protocol. You can now leverage the threat intelligence data in your security operations.